Government data shines a light on the most common forms of attack being suffered by organisations across the UK – with plenty of familiar foes featuring prominently. PublicTechnology crunches the numbers.
A central quandary facing those designing policy or laws for the online world is the extent to which it should be seen and treated as a separate entity, or whether it is an extension – or, perhaps, a reflection – of the physical realm.
The cybercrime landscape appears to lend support to the latter view; there are far more that are incidents are swift, blunt and opportunistic than those that are complex and carefully planned. Muggings are far more common that multimillion-pound heists.
Similarly, “the most common cyber threats are relatively unsophisticated”, according to the 2023 edition of government’s annual Cyber security breaches survey.
“Some of the cyber security breaches and attacks reported [here] would not constitute cybercrimes; some attempted attacks will not have penetrated an organisation’s cyber defences and some, such as online impersonation, would be beyond the scope of the Computer Misuse Act.”
Government Cyber security breaches survey 2023
The latest version of this in-depth research, published by the Department for Science, Innovation and Technology, reveals that about one in three businesses and a quarter of charities suffered a breach in the prior 12 months. The proportion rises significantly for larger organisations.
The study sheds further light on the most common forms of successful attack, and the devastation that can be wrought – even by “unsophisticated” means.
With data from 1,322 entities that reported a breach – drawn about two-thirds from the commercial world and one-third from the charity sector – the DSIT research ranked the most common threats by the percentage of victims that suffered such an attack.
Focusing on those that suffered a diverse range of incidents – by stripping out data from those that only encountered the near-ubiquitous phishing – the research also asked to rank which form or forms of attack delivered the greatest amount of disruption to their operations.
The most common impacts included loss of staff time and the need to implement new systems or processes, both of which resulted from about a quarter of successful attacks. A cyber breach halted work entirely for a time in 11% of cases, while about 2.5% lost revenue and encountered customer complaints, respectively.
As part of the PublicTechnology Cyber Security Week initiative – which today focuses on threats – PublicTechnology went through the data to rank the damage of each form of attack on UK organisations by plotting both its frequency and disruptiveness. Here’s what we found out.
Phishing
- Frequency – 80%
- Disruptiveness – 61%
Phishing attacks are – by a very, very long way – both the most common and the most disruptive security breaches suffered by UK organisations.
The government study defines phishing attacks involving “staff receiving fraudulent emails or being directed to fraudulent websites”.

It is a well-worn idiom that, in any organisation’s security set-up, ‘humans are the weakest link’. Expressing this sentiment – and the culture of blame and fear it is apt to perpetuate – is increasingly eschewed by cyber professionals, in favour of an approach that seeks to empower colleagues to embrace their security responsibilities.
But the truth the maxim speaks to is no less truer for that.
This is evidenced by the ongoing prevalence – and destructiveness – of phishing, the success of which can relies not of technical sophistication, but on appealing to humans through social and psychological expertise.
The research says: “One of the consistent lessons across this series of surveys has been the importance of organisations ensuring that their staff are aware of the risks, through training and other awareness-raising activities. This reflects that most cyber actors use social engineering techniques, as evidenced in the high prevalence of phishing attacks, to gain access to the target organisation’s networks.”
Others impersonating organisation in emails or online
- Frequency – 30%
- Disruptiveness – 36%
Breaches in which attackers successfully impersonate an organisation or one of its users are comfortably both the second most common and disruptive threats facing organisations – albeit a long way behind phishing.
The research notes that one of the complexities of such attacks – and other common threats – is that they may, under current legislation, not even be criminally prosecutable.
“Some of the cyber security breaches and attacks reported [here] would not constitute cybercrimes,” it says. “For example, some attempted attacks will not have penetrated an organisation’s cyber defences and some, such as online impersonation, would be beyond the scope of the Computer Misuse Act.”
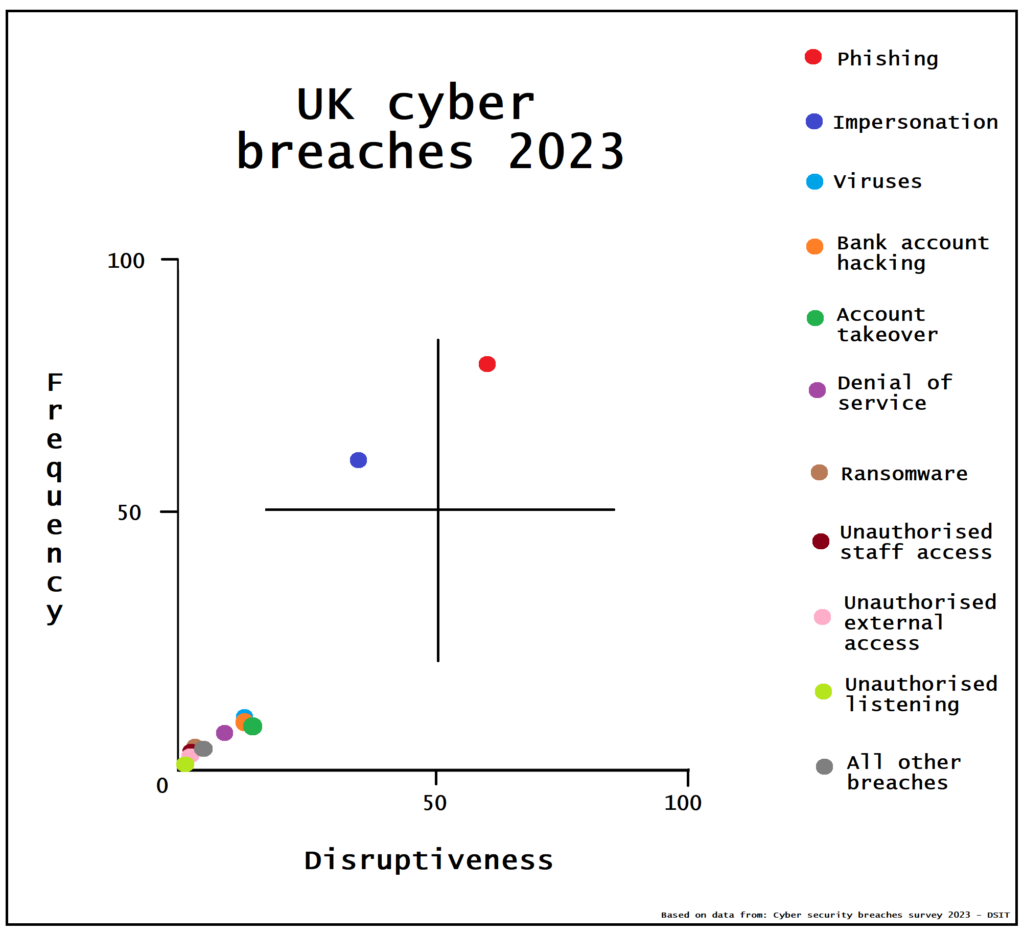
Viruses, spyware or malware
- Frequency – 10%
- Disruptiveness – 13%
The concept of the computer ‘virus’ has been something of a byword for cyberthreats for about four decades, and infecting a victim’s systems with programs that can wreak havoc remains a common – and often devastating – form of attack.
But, as organisations’ defences have improved – and phishing attacks have offered easier and richer pickings – the prevalence of malware and other viruses has declined significantly in recent years.
Since 2017 the proportion of UK firms and charities reporting a successful virus attack each year has fallen from one in three to one in ten.
Hacking or attempted hacking of online bank accounts
- Frequency – 9%
- Disruptiveness – 13%
Compared to the frequency of breaches in which bank accounts are successfully hacked, such attacks rate highly for the level of disruption they can cause.
The government research notes that hacked bank accounts are the, after phishing, the most common source of cyber-enabled fraud.
Denial of service attacks
- Frequency – 7%
- Disruptiveness – 9%
The study says that “denial of service attacks try to slow or take down organisations’ website, applications or online services, to render these services inaccessible”.
Such attacks – particularly in the form of large-scale and coordinated distributed denial of service assaults – have been suffered by some very high-profile victims over the years. This has often led to a level of publicity that, the research indicates, outstrips the prevalence of DoS and DDoS breaches.
The research notes that, while potentially destructive, these breaches represent the least common form of cybercrime – alongside another high-profile foe. Which brings us to…
Ransomware
- Frequency – 4%
- Disruptiveness – 3%

The spectre of ransomware may, for many, have become the archetype of what a cyberattack looks like. Many of the most prominent – and most catastrophic – breaches in recent years have involved the successful deployment of ransomware.
This includes WannaCry: the most severe attack ever to have hit the UK, which caused 19,000 NHS appointments to be cancelled or postponed, and left the health service facing a long period of tech disruption – and recovery costs of £92m.
Unauthorised accessing of files or networks by staff
- Frequency – 3%
- Disruptiveness – 2%
Insider threats – in which staff deliberately and maliciously misuse company systems or data – are another high-profile form of breach, and many organisations strive to manage the threat they pose with rigorous policies.
But, as the research makes clear, cases of employees getting into places they should not are comparatively rare.
Unauthorised accessing of files or networks by outsiders
- Frequency – 2%
- Disruptiveness – 2%
Rarer still is external attackers gaining access or organisations’ date or networks. The image of a hacker malignantly – and expertly – picking organisations’ technical locks may spring to many people’s minds when the concept of cyberattacks is invoked.
However, they are comparatively seldom able to do so, the study indicates. This is perhaps a reflection of improvements in organisations’ defences. But also of the comparative ease of other forms of attacks; why wait for cover at night to try and sneak in through a window when, with a successful phishing campaign, you can effectively walk in through the front door in broad daylight?
Unauthorised listening into video conferences or instant messages
- Frequency – 0.7%
- Disruptiveness – 0%
The use of videoconferencing tools and instant messages may have rocketed up as a result of the Covid pandemic but these tools are, clearly, yet to become a fruitful target for cyberattackers.





What抯 Happening i’m new to this, I stumbled upon this I have found It positively useful and it has aided me out loads. I hope to contribute & help other users like its aided me. Good job.
It抯 really a cool and helpful piece of information. I抦 glad that you just shared this helpful info with us. Please stay us up to date like this. Thank you for sharing.
One more thing to say is that an online business administration training is designed for scholars to be able to efficiently proceed to bachelor degree courses. The 90 credit certification meets the other bachelor college degree requirements and when you earn your current associate of arts in BA online, you will have access to the most up-to-date technologies in this field. Some reasons why students have to get their associate degree in business is because they can be interested in this area and want to find the general knowledge necessary ahead of jumping right bachelor college diploma program. Thanks for the tips you really provide inside your blog.
amazing blog! since i checked out yours, care to checkout mine? its all about kanye west posters https://sneakerxp.com/communications-mobile-phones/everyone-loves-kanye-west-poster/
Sweet blog! I found it while browsing on Yahoo News. Do you have any tips on how to get listed in Yahoo News? I’ve been trying for a while but I never seem to get there! Thank you
I actually wanted to type a simple message so as to express gratitude to you for all the marvelous information you are posting at this site. My considerable internet search has now been recognized with high-quality concept to go over with my friends and classmates. I ‘d express that many of us readers are undeniably fortunate to live in a perfect network with very many special people with beneficial strategies. I feel truly privileged to have encountered the web page and look forward to so many more exciting times reading here. Thanks a lot once more for a lot of things.
하동동해출장만남 소자본 창업
A great post without any doubt.
Nice i really enjoyed reading your blogs. Keep on posting. Thanks
벼룩시장 구인구직 및 신문 그대로 보기 (PC/모바일) | 구인구직 앱 어플 무료 설치 다운로드 | 모바일 벼룩시장 보는 방법 | 벼룩시장 부동산 | 지역별 벼룩시장 | 벼룩시장 종이신문 에 대해 알아보겠습니다. 섹스카지노사이트
Hello. excellent job. I did not expect this. This is a impressive story. Thanks!